...
Action/Resource | Collection | Object | Datastream |
|---|---|---|---|
Create | Add new objects to this collection | Add new datastream to this object | N/A |
Read | View, search, browse all objects (including sub-collections) in this collection | View, search and browse this object | View, search, browse this datastream |
Update | Same as "create" but also includes renaming this collection and deleting objects from this collection | Same as "create" but includes deleting datastreams and modifying the object's properties | Modify the current datastream |
Delete | Delete the collection including its children | Delete the current object | Delete the current datastream |
Publish | N/A | Make the current object search-able and browse-able | N/A |
Admin | Set access policy for this collection | Set access policy for this object | Set access policy for this datastream |
...
With the Policy Editor, you can specify two type of permissions: simple and advanced. Simple access control, as the name indicates, allows you to assign concrete permissions such as "read", "write" and "publish" to users or a group of users (role). With advanced policies, you can create complex and powerful access control rules such as "allow public users to read all PDF datastreams of this object" or "denied access to all Word documents created by Joe Bloke"...
Basic Permissions
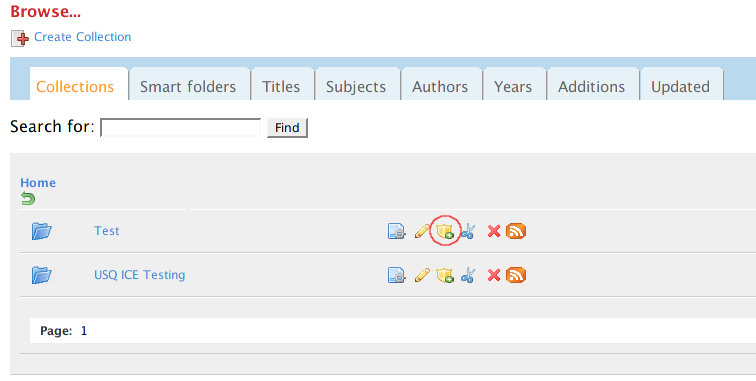
Once the "Edit Permission" icon is clicked, the following screen will be presented to users:
...
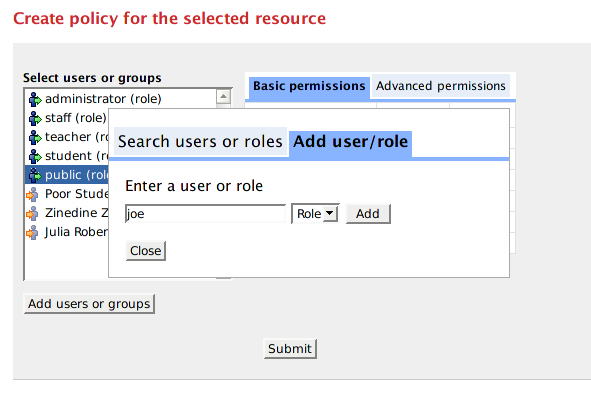
You can add arbitrary users/roles by clicking on "Add User/Role" tab.
Advanced Permissions/Policies
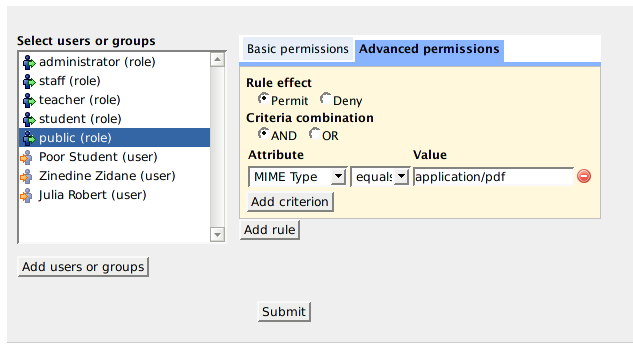
In order to specify advanced policies for a particular user/role, select that user/role in the list box and click on "Advanced Permissions" tab on the right hand side. The following will be presented to you:
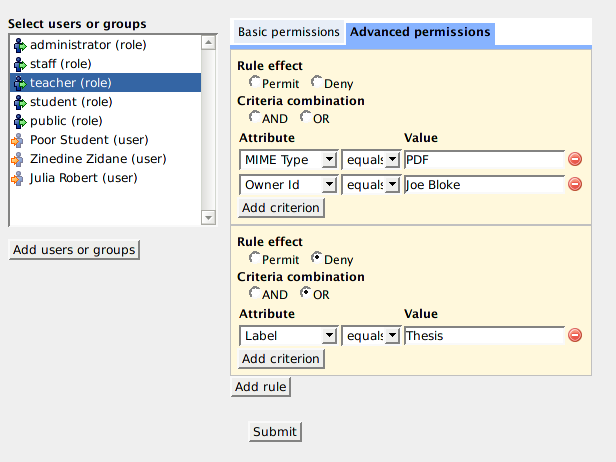
Muradora will try to load any existing advanced policies assigned to the selected user/role for current object. An advance policy consists of multiple rules each of which has multiple criteria. Criteria are used by XACML engine to determined whether a request matches a rule. Examples of criteria are "MIMETYPE equals PDF" or "OWER_ID equals JOE BLOKE"... The effect of a rule can either be "Permit" or "Deny". If an advanced policy has multiple rules then its effective effect will be determined by the combination algorithm of the XACML engine.
Access Control Policy Precedence
Default Access Control Settings
...