...
The essential idea of CIS is combining hash value of document with other hash values received in the same time period to create a witness hash value. This kind of linking makes it computationally infeasible for an adversary to back-date a document, since that would entail computing hash collisions for the witness values. This technique relies only on the collision resistance properties of hash functions, and does not have any secrets or keys that need to be securely protected over extended periods of time.
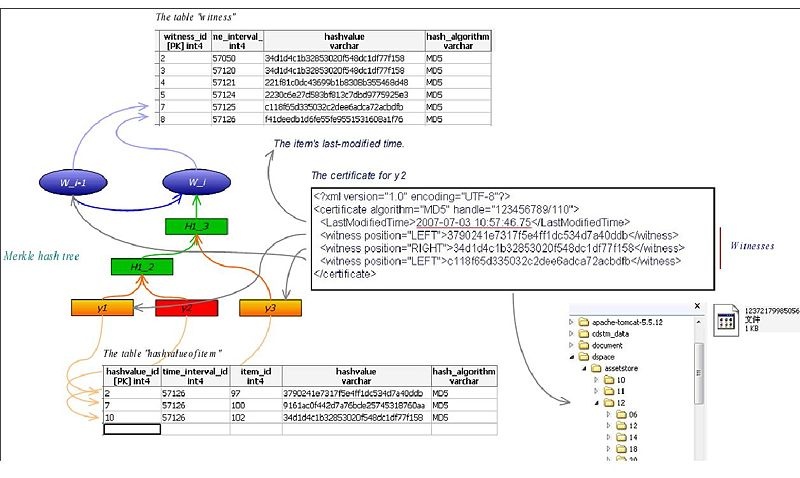
The picture below shows approximately how CIS works:
As this picture illustrates, items y1, y2, and y3 were received in a time interval. The process producing y2's certificate could be described like this:
...
- Make a tool generating certificates manually for items.
- Make the UI more friendly with Ajax.
See Also
Wiki Markup \[ Project abstract\|http://code.google.com/soc/dspace/appinfo.html?csaid=11628C0CA9FCEC61\]
- A Content Integrity Service For Long-Term Digital Archives
- Hashing function APIs in JDK
- AJAX Tutorial